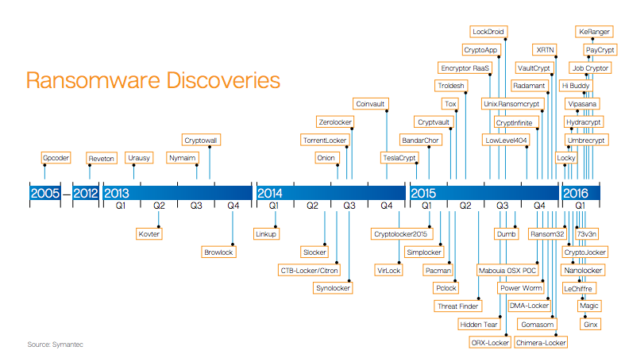
As you may have noticed, Ransomware is one of the trending topics in security talks around the internet. And there is a reason for it; In the US alone, already 2,500 cases of ransomware were reported to the Internet Crime Complaint Centre in 2015, costing victims $24 million. And in the first quarter of 2016, Ransomware attacks quadrupled according to Symantec.
With the release of more and more new variants of Ransomware, it remains difficult to protect your corporate network against these significant security threats. (Even when you have all the security best practices in place). Therefore, besides having the tools to protect your network from malware infections, monitoring and alerting is of equal importance.
The biggest risk lies in new (and undetected) malware
Over the past months we have discovered that some of our clients who had all the best security best practices in place, were still affected by some new viariants of Ransomware. After analysis, we discovered that these new Ransomware variants were so new that they were not discovered by the traditional Antivirus tools, and even though the infection was only limited to one or two machines, they were able to infect the shared folders on the customers server, encrypting thousands of files. With good backups, it is possible to recover from these attacks, however it usually results in significant downtime for organizations, as they need to identify the source of the infection, eliminate it, and then restore the entire file server content from backups. Therefore it is important to have tools in place that alert you when an infection is taking place, and where it is coming from, even if it is not detected by your antivirus system. There are several solutions that you can assist you with this alerting and identification or possible threats. We will list out two examples that we have implemented for our customers.
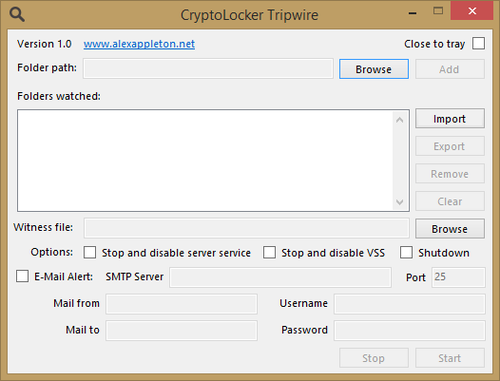
Cryptolocker Tripwire
Cryptolocker Tripwire has been developed a few years ago, free of charge, but can be still effective in alerting and limiting a ransomware outbreak. The software uses one or more witness files that are placed in the shared network folders of your organization. The software monitors these files on a constant basis and can send out an alert and/or shut down the file sharing services when it detects a modification to these witness files.
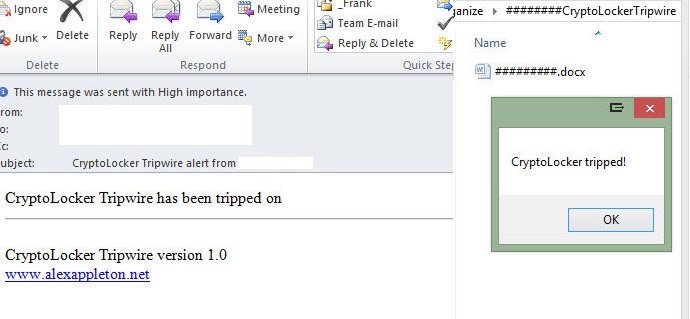
For example, if there were an Ransomware outbreak that started to infect the shared folder on the network, it would find these witness files and will encrypt them, triggering an alert from CryptoLocker Tripwire, which will then send an email to the administrator group and shuts down the file sharing service.
There are some limitations of this software, such as the fact that it cannot be started as a service. However, as it is a free software, it may be a cost effective solution for companies to implement as an additional security measure.
More information can be found here: http://alexappleton.net/post/83785313416/download-cryptolocker-tripwire-10
ManageEngine ADAudit Plus
The ADAuditPlus software from ManageEngine can be used to monitor an extensive range of Active Directory properties, such as user logon activity, object access, account privilege changes on Domain Controllers, and has pre-configured audit reports and email alerts.
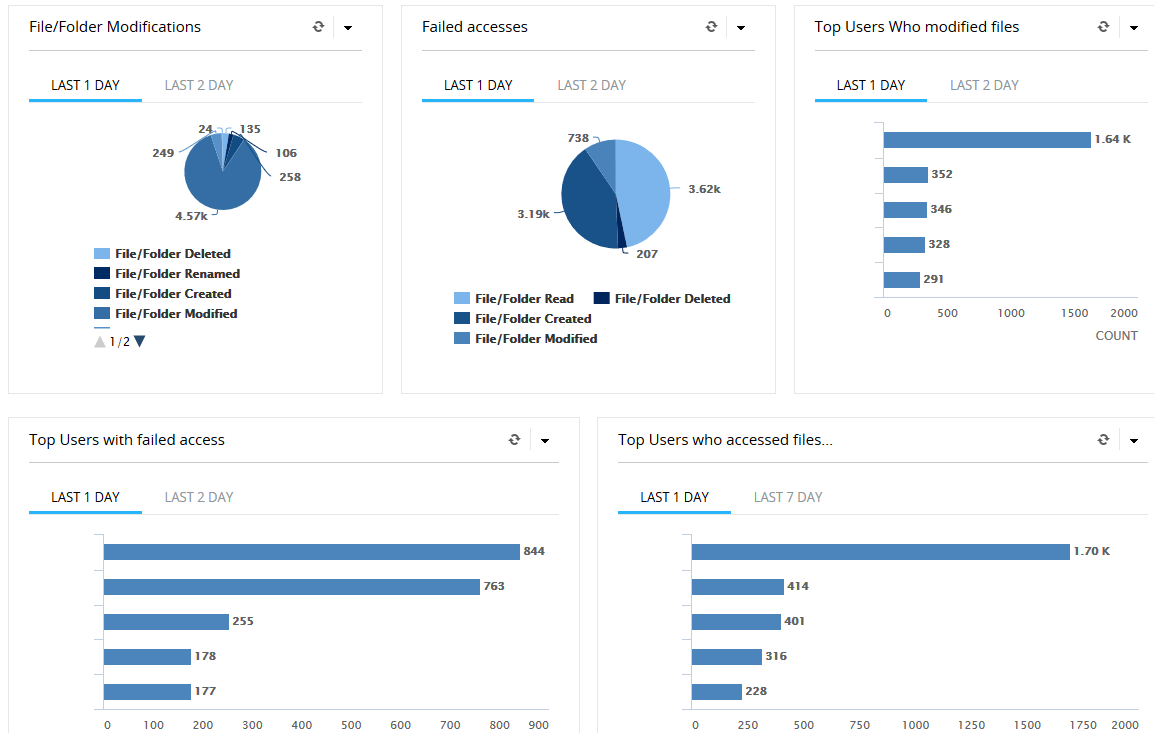
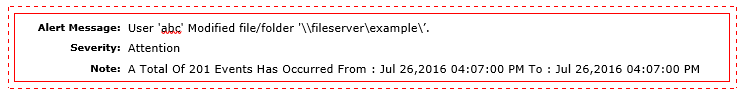
The file/folder auditing function can be used to monitor all changes on your servers file shares. For example, if a Ransomware infection has started to encrypt your network files, you can view the log files and find the user or computer where the infection originated. It also shows a complete log of which files have been modified with the ransomware, so you know exactly which files or folders you need to restore. ADAudit Plus also has the feature to alert the IT administrators by email in case of certain events. For example, it is possible to have ADAudit send out an email alert if over a certain files (for example 200) have been modified in a short period of time. In this case it is possible to identify a malware attack in an early stage.
More information about ADAudit Plus can be found here: https://www.manageengine.com/products/active-directory-audit/
These are just two examples of different ways to improve your resilience to Ransomware attacks, and there are more tools out there such as EventSentry and some new initiatives such as CryptoDrop. The AccessOrange team can help you identify what is the best solution for your organization and implement the tools necessary to protect your business critical data. For more information, contact us at [email protected]